Getting Acquainted with Cryptocurrency Wallets and Ensuring Their Security
Introduction
The security of a cryptocurrency wallet encompasses a wide range of considerations, with potential vulnerabilities and threats often emerging at the convergence of multiple factors. These factors span design, security protocols, cryptography, access control, authentication methods, and storage practices. Among all elements in the crypto ecosystem, safeguarding private keys reigns supreme in importance. Mishandling private keys is akin to entrusting a malevolent actor with the keys to your safety deposit box.
While individual vulnerabilities may not necessarily lead to security breaches on their own, the threat landscape can significantly expand when these issues compound. Unlike traditional banks and even certain centralized crypto platforms, public blockchains lack the safety nets of anti-fraud mechanisms, customer support, or transaction reversals in cases of compromised funds.
This article is designed to demystify the essential terminology related to wallet security, outlining the various threats and risks faced by both end-users and developers in the crypto wallet realm.
Essential Terminology and Concepts in Wallet Security
A cryptocurrency wallet serves the purpose of signing transactions and safeguarding the private keys essential for interacting with the blockchain network. Within a wallet, there exist a public key (referred to as the wallet address) and a private key, which is indispensable for executing and validating transactions. Control over the private key equates to control over the stored assets.
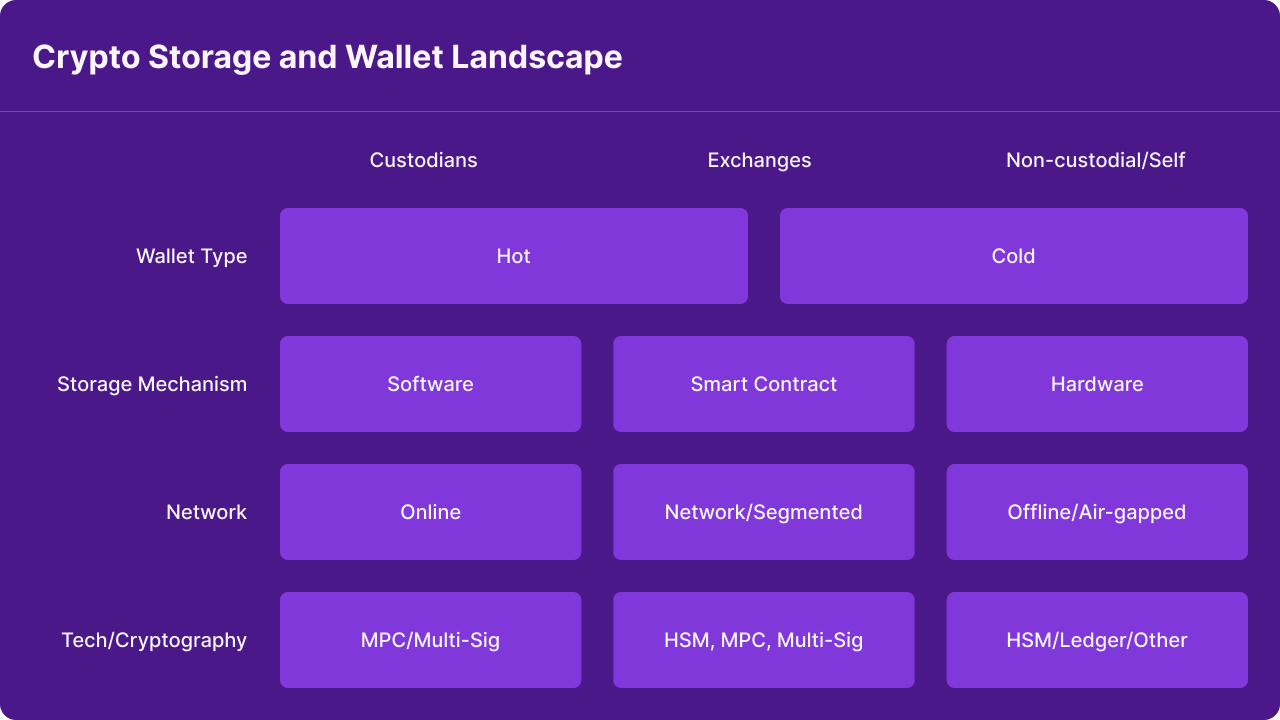
There are various categories of cryptocurrency wallets accessible to both individuals and organizations, each offering a distinct level of security. Depending on the requirements for storing assets, one might opt for a single wallet type or a combination of them:
Custodial Wallet: In this arrangement, a third party, such as an exchange or custodian, assumes responsibility for managing the account/wallet's private keys, assets, and overall security. Notable examples include Coinbase, BlockFi, and Gemini.
Non-Custodial Wallet: Non-custodial wallets grant complete control to the user, whether they are individual or institutional users. Users are exclusively accountable for the wallet's security, private keys, and the assets contained within. Prominent instances encompass Fireblocks, decentralized autonomous organizations (DAOs), and Gnosis Safe.
Hot Wallet: These wallets maintain some form of internet connectivity, whether through mobile or web interfaces. Notable examples include Coinbase Wallet, Metamask, and Phantom.
Cold Wallet: Cold wallets are characterized by their offline nature, which can take the form of hardware devices or paper wallets. They are intentionally isolated from the internet, offering heightened security. Well-known cold wallet brands include Ledger and Trezor.
Smart Contract Wallet: These wallets are accessed and managed through smart contract code. Two subtypes exist: externally owned accounts, accessible via a private key or seed phrase, and contract accounts, which are governed by smart contracts. They closely resemble traditional financial applications and may incorporate features such as multi-signature authorization, account freezing, transaction limits, two-factor authentication (2FA), allow listing, and guardians. Examples in this category include Argent and Gnosis Safe.
It's crucial to emphasize that even though exchange wallets fall under the hot wallet category, they are custodial in nature. This implies that a third party has complete control over key management and wallet security, assuming full responsibility for these aspects.
Seed Phrases & Private Keys
Seed phrases and private keys play pivotal roles in every wallet, irrespective of its controller. They both serve as access keys to your cryptocurrency wallets and accounts, granting the authorization for wallet access. While they share similarities, it's important to recognize that seed phrases and private keys have distinct characteristics and are not interchangeable.
Private Key - This is the access key represented as a hexadecimal value. It serves as the key to access the specific underlying asset address (e.g., Bitcoin). The asset address functions as the storage account for a particular asset. To gain complete access to the asset address, the correct private key is required.
Seed Phrase - Introduced in 2013, the seed phrase was developed to convert access keys into words, giving rise to the concept of a mnemonic phrase. A seed phrase acts as the master access key for your cryptocurrency wallet. Additionally, seed phrases serve as backups for your wallet. They encompass both access keys and instructions for the wallet, detailing how and which accounts to set up.
To ensure the security of your assets, it's imperative to back up and store both your seed phrases and private keys offline. Digital copies are vulnerable to various digital threats. Instead, opt for non-digital copies, such as writing them down on paper or using crypto steel. Crypto steel is a stainless steel device designed for storing your seed phrases and private keys. It serves as a durable, waterproof, tamper-proof, and fireproof solution. Numerous variations and brands of crypto steel exist, but they all share the fundamental goal of securely storing your private keys and seed phrases offline.
Multi-Party Computation vs Multi-Signature
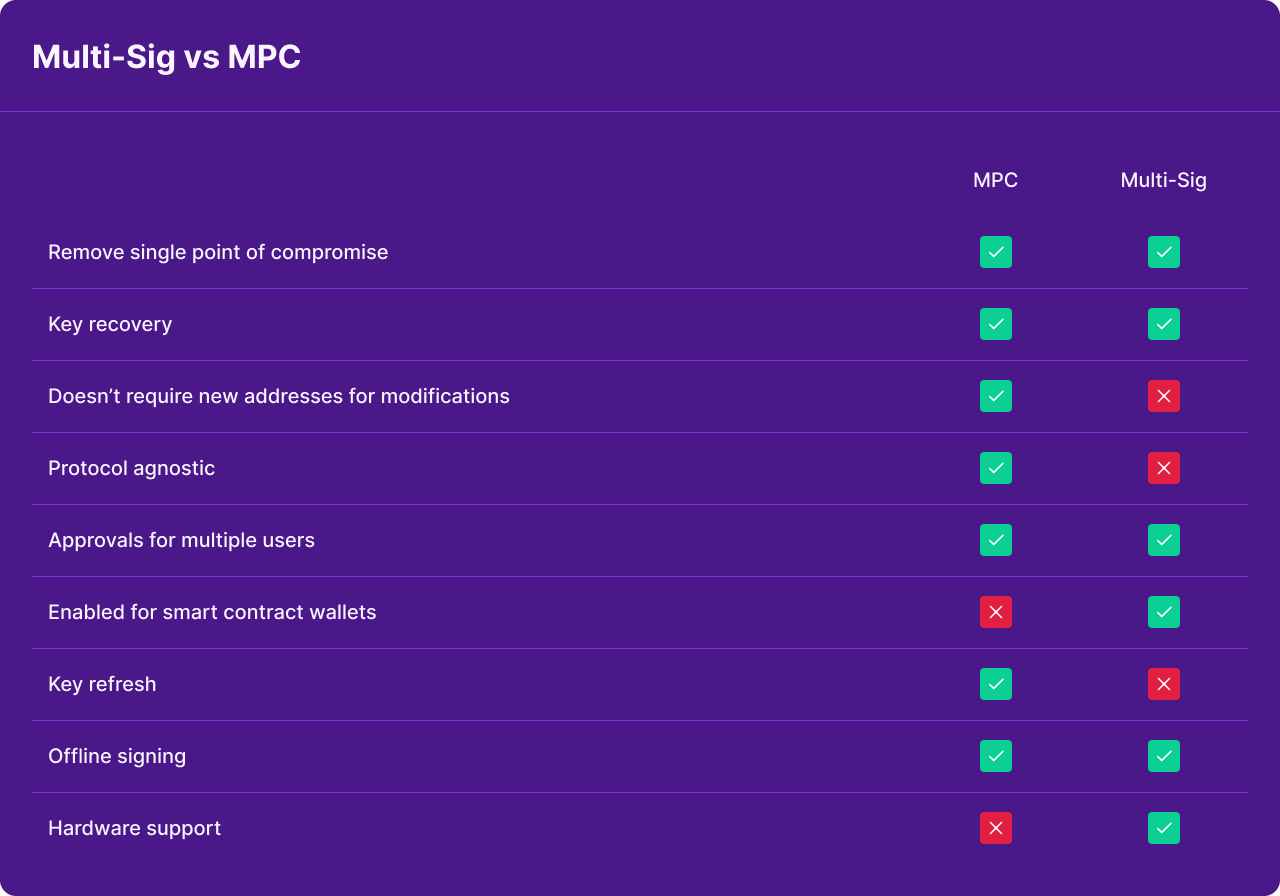
Digital signature schemes are a pivotal element of wallet security, serving as a fundamental component of blockchain technology. Their primary role is to authenticate transactions within the blockchain. In the realm of crypto wallets, two prevalent digital signature schemes are Multi-Party Computation (MPC) and Multi-Signature (Multi-Sig). The ongoing debate over MPC vs. Multi-Sig centers on their respective security merits, but it's essential to understand that each has its own set of trade-offs, with overall security hinging on design and implementation.
MPC (Multi-Party Computation) - Opting for MPC ensures the absence of a single point of failure. It ensures that a complete private key is never consolidated during creation or during the signing process. Instead, private keys are fragmented into shares, encrypted, and distributed. This fragmentation is achieved through the randomization of individual secrets. Importantly, these secrets are never concentrated on a single device at any given time. Typically, there are more than three endpoints, spanning servers or mobile devices, and each of these endpoints guards its respective secret closely. These endpoints collaborate in a decentralized wallet creation protocol, culminating in the computation of the public key corresponding to the set of individual private shares (usually three). When a transaction requires a signature, a quorum of endpoints, typically three or more, participates in a distributed signature process. Each endpoint independently validates the transaction and its associated policy before signing the transaction.
Multi-Sig (Multi-Signature) - Multi-Sig introduces an additional layer of security compared to a single key that can access funds. It enables two or more individuals or devices to collectively sign transactions. Similar to MPC, Multi-Sig eliminates the risk associated with a single point of failure. However, challenges arise in terms of interoperability and protocol agnosticism. Not all cryptocurrencies or DAOs support Multi-Sig, as each protocol mandates wallet providers to implement distinct code. Therefore, the creation of new wallets may be required to modify quorums and refresh keys. This challenge initially emerged when Bitcoin was the primary currency, and it has persisted as different protocols introduced their own complexities. Due to some of the limitations associated with Multi-Sig, securely supporting new assets can be challenging, and managing multiple implementations across different blockchain networks can be a demanding task to oversee.
Wallet Vulnerabilities & Threats
Vulnerabilities and threats in the realm of crypto wallets can be specific to the wallets themselves, the devices or operating systems hosting them, or a combination of both. True wallet security necessitates a comprehensive approach that integrates security measures across the wallet application and the underlying device or platform.
Mobile App Wallets - Wallets designed for mobile devices are susceptible to mobile-specific vulnerabilities. Many applications, including crypto wallets, lack the ability to verify if a device is trustworthy, rooted, jailbroken, or compromised by malicious software. Mobile malware can exploit these vulnerabilities to pilfer users' credentials, seed phrases, or private keys stored in the application's memory. In cases where wallet apps do not mandate a device-level passcode, attackers may easily unlock the device or access keychains and key storage.
Web/Browser-Based Wallets - Web and browser-based wallets face a myriad of potential threats. Browsers are common targets for exploits and zero-day vulnerabilities that can grant attackers access to system memory. Phishing attempts are also prevalent, wherein malicious actors create counterfeit transaction screens, such as "import account" or "send transaction," to deceive users. Another common attack involves replacing the content of the clipboard with the attacker's wallet address.
Exchange/Custodial Wallets - Exchange or custodial wallets, being entirely controlled by third-party entities, are exposed to a wide array of threats. These entities must implement enterprise-wide security measures, encompassing key management, application security, data security, and more, to safeguard users' funds and information. Users place their trust in these organizations to manage their wallets and data. Additionally, users who utilize custodial services are vulnerable to phishing scams that can harvest their login credentials.
Cryptographic Operations - Crypto wallets perform numerous cryptographic operations, and while many are derived from the cryptography community, room for error remains. Cryptographic code can suffer from design flaws and implementation errors, necessitating a specialized development skill set. Cryptographic issues often result from a combination of design and implementation mistakes.
DeFi and Decentralized Apps - Many wallets integrate with decentralized applications (dApps), introducing various threat vectors. These include communication between the wallet and the dApp, the potential for malicious dApps, and platform risks for both web and mobile interfaces. Attackers may intercept and modify requests due to inadequate authentication, insufficient data-in-transit encryption, and improper authorization of transaction data. Even dApps from ostensibly "trusted sources" could be compromised or maliciously altered. Additionally, most blockchains and wallets lack robust anti-spam or anti-abuse protocols, making them susceptible to fraudulent requests from malicious dApps.
Third-Party Libraries and Dependencies - Crypto wallets frequently rely on third-party libraries and dependencies, some of which may have access to sensitive wallet data, including private keys. If any of these libraries or dependencies contain vulnerabilities, it can expose the entire wallet to these vulnerabilities or potentially more severe security risks.
Optimal Strategies and Universal Security Guidelines for Wallets
How Users Can Enhance Wallet Security:
Password Management: Employ a password manager to generate and store complex, unique passwords securely. Strong passwords often don't require frequent changes, but if you suspect a compromise, update your passwords and enable 2FA immediately. Never reuse passwords, especially for sensitive accounts like banking, cryptocurrency, or email.
Two-Factor Authentication (2FA): Activate 2FA for all your accounts.
Dedicated Email Addresses: Use distinct email addresses, specifically for sensitive accounts related to banking, cryptocurrency, and similar services. This widens your defense against potential threats.
Secure Storage of Seed Phrase: Safeguard your seed/recovery phrase offline and create multiple copies. Split the phrase into two parts and store them separately, such as in safety deposit boxes.
Hardware Wallets: Employ a secure hardware wallet and store it in a safe location.
Regular Updates: Keep your browsers, devices, and operating systems up to date to patch vulnerabilities.
Email Verification: Verify the sender's email address before responding or sharing any information.
Allowlisting: Enable allowlisting on all wallets and accounts to specify trusted sources.
Private Seed Phrase: Keep your seed phrase private and off devices.
Protect Your Private Key: Do not share or expose your private key to anyone.
Trusted Hardware Wallet Purchases: Only purchase hardware wallets from reputable vendors and directly from the official vendor's website.
Secure Delivery: When buying hardware wallets online, use services like Amazon lockers for delivery to protect your home address from potential data breaches.
Prefer App-Based 2FA: Avoid SMS authentication and opt for app-based 2FA methods.
Limited Wallet Connection: When connecting your wallets to dApps or third-party sites, only keep your wallet connected for the duration of use. Disconnect it as soon as you finish.
Diversify Holdings: Avoid keeping all your cryptocurrency or NFTs in a single wallet. Diversify your holdings across multiple wallets for added security.
Burner Wallets: Use burner wallets for connections to unfamiliar sites or for minting/airdrops. You can transfer assets to a more secure, long-term storage wallet after collecting them.
How Developers Can Build Secure Wallets:
Network and Ecosystem Understanding: Gain a comprehensive understanding of the network and ecosystem in which you're developing. Risks associated with crypto wallets can vary across different blockchains, platforms, and applications, and can even differ for each cryptocurrency asset.
Selecting the Right Wallet Type: Choose the wallet type that aligns with your application's requirements. For swift asset movements, hot wallets are suitable due to their speed but are generally less secure as they are connected to the internet. If immediate asset processing isn't necessary, opt for cold storage for enhanced security.
Digital Signature Scheme Choice: Deciding between Multi-Party Computation (MPC) or Multi-Signature (Multi-Sig) is a design decision that often involves trade-offs between speed, cost, and security. Keep in mind that an insecure digital signature scheme can compromise the overall security of your wallet implementation.
Balancing Act: Maintain an appropriate balance in hot wallet balances to ensure an acceptable level of risk.
Custodial/Non-Custodial Solutions: If you're using a custodial or non-custodial solution, have a robust backup and recovery plan in place. Ensure you can reassemble key shares to unilaterally move assets. Enable 2FA on all accounts, implement strong password policies, and establish secure protocols for all asset transfers.
Adding Friction for Sensitive Actions: Enhance end-user security by adding friction to sensitive actions. Require passwords or PINs for activities like fund transfers, provide helpful hints, and display warnings when necessary.
Secure Software Development Lifecycle (SDLC): Follow Secure Software Development Lifecycle practices (SDLC) and leverage Static Code Analysis (SAST) tools to identify vulnerabilities early in the development process.
Dependency and Library Review: Thoroughly review all dependencies and libraries before integrating them into your project.
Regular Audits: Conduct audits and continuously monitor libraries and dependencies whenever possible.
Cryptography Best Practices: Adhere to best practices in cryptography. Avoid implementing custom ciphers or protocols, use robust encryption, and securely store sensitive keys, such as private keys. It's advisable to keep private keys or signing keys separate from the application used for asset processing. Consider using secure enclaves or trusted execution environments for signing and decrypting private key material.
Security Emphasis: Prioritize security and protection against large-scale exploits.
Transport Encryption: Implement strong transport encryption for integrations and communication.
Tamper Protection: Incorporate tamper protection mechanisms for wallet applications and provide alerts to users if the device is deemed untrusted.
Device Passcodes: For mobile-based wallets, require users to set up device-level passcodes and send reminders for this security measure.
Device Restrictions: Limit wallet functionality on rooted or jailbroken devices.
Up-to-Date OS/Devices: Be cautious about supporting outdated operating systems or devices.
Secure Storage: Utilize native, secure storage options to minimize the lifecycle of sensitive data.
Proper Crypto Primitives: Implement correct cryptographic primitives.
Strong Key Management: Adhere to robust key management practices.
Memory Management: Ensure secure memory management of secrets.
Conclusion
Security for crypto wallets presents a multifaceted challenge within the crypto infrastructure, and safeguarding wallet assets is paramount. The realm of potential attacks on crypto wallets is extensive, making them an attractive target for malicious actors. To ensure the safety of assets, it's imperative to adopt a comprehensive perspective on wallet security. Any amalgamation of vulnerabilities, suboptimal design choices, or errors has the potential to culminate in the loss of funds.
I'd love to connect with you on Twitter | LinkedIn | Portfolio.
About QuickNode
QuickNode is building infrastructure to support the future of Web3. Since 2017, we've worked with hundreds of developers and companies, helping scale dApps and providing high-performance access to 24+ blockchains. Subscribe to our newsletter for more content like this, and stay in the loop with what's happening in Web3!
